Firepower 6.2.0 Release
After some delays version 6.2.0 has been released for Cisco Firepower Systems. The version brings some long awaited and desperately needed features I have been waiting for quite some time. Lets jump right into what is new, what has changed and why FlexConfig should die a fast and swift death again.
What is new
ASA to FTD Migration Tool
Migrating from Cisco ASA to Firepower Threat Defense can be a daunting task for customers with multiple access control lists (ACLs), NAT policies, and related configuration objects. The migration tool is specifically designed to assist this migration process. The tool allows you to convert ASA configurations (ACL, NAT and related objects) to Firepower Threat Defense configurations, which you can then import into the Firepower Management Center. The migration tool supports the conversion of up to 600,000 total access rule elements per ASA configuration file.
Comment
A migration tool for ASA to FTD was already available in 6.1 for partners but there was only so much it could do. Using the migration tool we can move existing ASA configuration with minimum version 9.1.x and dont need to tinker around with migrating large ACLs, NAT policies and objects manually. I would have been more happy if they just provided a script to export from ASA using REST and import into FMC using REST but since the FMC API is still lacking with only a few CRUD operations being available we will have to wait for 6.2.1 to finally use it to create static routes and edit our NAT policy on FMC.
The reason I would prefer an open api approach to this is because I want to migrate ANY firewall vendor to FTD without hassle. If Cisco would provide a reference implementation for ASA and would invest more into FMC API we could write our own tooling to get this done.
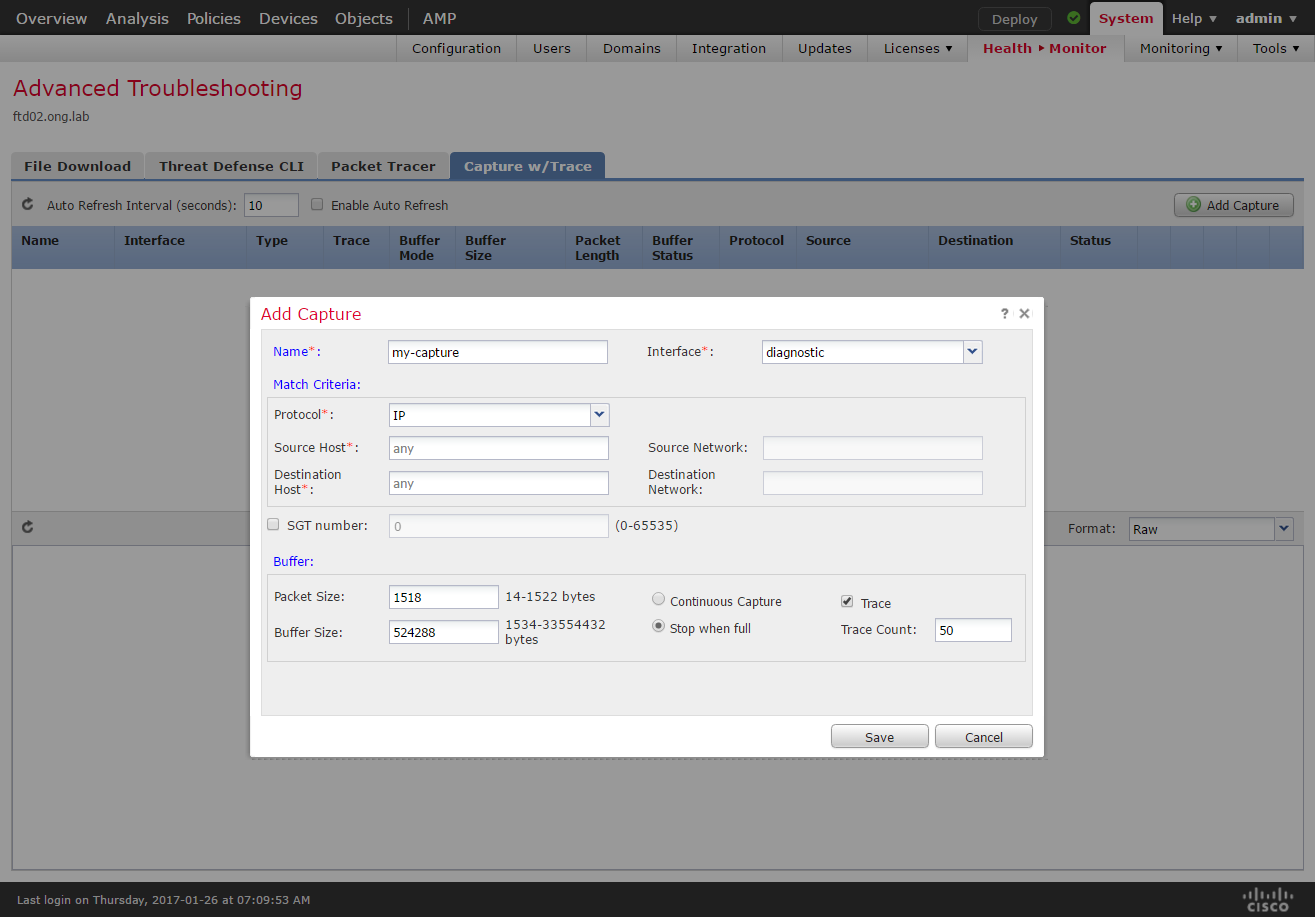
Packet Tracer and Capture
The Packet Tracer and Capture offers the ability to show all the processing steps that a packet takes, the outcomes, and whether the traffic is blocked or allowed. This allows users to initiate and display output of tracing from the Firepower Management Center. The tracing information includes information from SNORT and preprocessors about verdicts and action taken while processing a packet.
Comment
This feature in itself is not exactly new but before 6.2 there was no available method to capture on FTD from the FMC UI. You would have to go to the CLI and capture using the trace option on lina. To capture traffic using FMC goto Health > Monitor, select your FTD device and click the advanced troubleshooting button.
Integrated Routing and Bridging (IRB)
Customers often want to have multiple physical interfaces configured to be part of the same VLAN. The IRB feature meets this demand by allowing users to configure bridges in routed mode, and enables the devices to perform L2 switching between interfaces (including subinterfaces).
Comment
Finally. We have been waiting for bridging support since the release of ASA 5506-X. This feature is not needed in larger environments but try to sell an additional switch to a small business because your eight port firewall has no switching support.
Inter-chassis Clustering
Clustering lets you group multiple FXOS chassis ASAs together as a single logical device. A cluster provides all the convenience of a single device (management, integration into a network) while achieving the increased throughput and redundancy of multiple devices. In Version 6.2, the Firepower System supports clustering across multiple chassis (inter-chassis clustering), allowing for higher scalability. You can use the Firepower Management Center to automatically discover all nodes of a cluster. (only supported on 4100 / 9300 appliances with up to 6 modules)
Comment
Hooray for feature parity, but to be honest I wouldnt recommend Inter-Chassis clustering as of now because I have had enough issues with Active/Standby HA on FTD already that I would not trust a dot zero release with such a mission critical feature. Definitely a feature to look into if you need to scale out to multiple 9300 chassis but then again if you have so much East-West traffic, a central firewalling solution might not be the right solution for you.
FTDv on Microsoft Azure
In Firepower Version 6.2, Cisco Firepower Threat Defense Virtual is available in the Microsoft Azure Marketplace. This new platform enables you to secure workloads consistently across the data center and public cloud. Managed centrally by an on-premises Firepower Management Center, Firepower Threat Defense Virtual provides advanced threat protection in the Azure environment without forcing customers to backhaul traffic to the data center.
Comment
Good to see additional support. Since many customers are migrating to Public Cloud, knowing that FTD is supported on the big players platforms is nice to see. Keep in mind that FMC is still not supported on Azure which I found to be quite weird. Try explaining to somebody that he can use Ciscos NGFW on Azure but he cannot host the management there as well.
PKI Support for Firepower Management Center
Public Key Infrastructure (PKI) is required to create certificate-based trusted identities for devices establishing site-to-site VPN tunnels. This feature allows you to associate PKI certificate data with devices via the Firepower Management Center.
User-based Indications of Compromise (IOCs)
This feature allows you to generate user-based IOCs from intrusion events, or view the associations of users and IOCs. You can also enable and disable eventing of a given IOC per user (against false positives). With this feature, you can correlate IOCs and events to both hosts and users, plus give them more visibility and alerting options on a per-user basis.
Comment
Associating IOCs is a really good idea. IOCs associated to Hosts were ok, but if you are dealing with users, IPs will change and keeping track of this automatically on the system helps a lot.
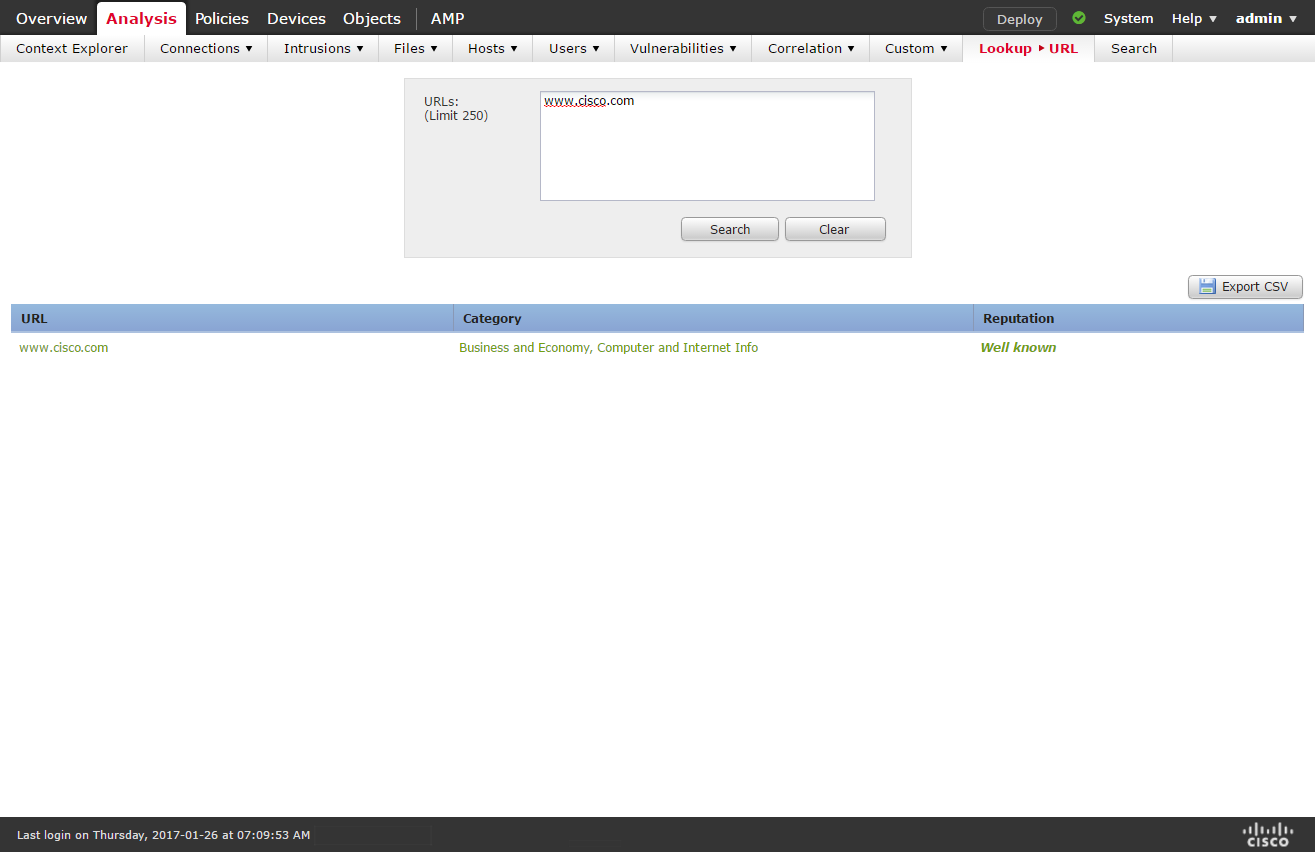
URL Lookups
This feature allows you to perform a bulk lookup of URLs (up to 250 URLs at a time) to obtain information, such as reputation, category, and matching policy. You can also export the results as a file of comma-separated values. The feature reduces the manual work necessary to determine if your organization is protected against a malicious URL or if you should add a custom rule for a specific IOC. You can use this feature to reduce the number of custom rules, which in turn reduces the chance of performance degradation due to extensive custom rule lists.
Comment
This will definitely be a time-saver when troubleshooting URL Filtering related issue. On a side note I would really like to see options for Block Pages to include information like Category, Reputation, etc. Not knowing why content was blocked is annoying for users.
FlexConfig
The FlexConfig feature allows you use the Firepower Management Center to deploy ASA CLI template-based functionality to Firepower Threat Defense devices. This feature allows you to enable some of the most valuable ASA functions that are not currently available on Firepower Threat Defense devices. This functionality is structured as templates and objects that are stitched together in a policy. The default templates are officially supported by Cisco TAC. The targeted features unlocked by FlexConfig potentially include:
- Non-Inspection Templates:
- Routing (EIGRP, PBR, and IS-IS)
- Netflow (NSEL) export
- MPF connection limits, timeouts (including DCD), and Normalizer settings
- Platform sysopt commands
- Proxy ARP Neighbor Discovery (sysopt noproxyarp interface)
- Pv6 Prefix Delegation
- IPV6
- WCCP
- VXLAN
- Application Layer Inspection Templates:
- ALGs default configuration
- GTPv1/v2 support
- Diameter inspection
- LISP inspection
- SCTP support and inspection
- SIP
- SS7 inspection
Comment
Finally. We can use MPF to edit tcp parameters… I really needed this feature so bad for applications that cannot use tcp keep-alive to keep sessions open and just got an idle-timeout after 60 minutes. While I am happy that we can now use a hacky method to configure missing features I am equally disappointed to see something like FlexConfig in 2017. It is a hack to solve an issue that shouldnt have existed in the first place. If Cisco just invested more time in a REST interface for ASA and built the FMC integration using mentioned API and not the legacy CSM code that just pushes CLI configuration into devices I think we would not have this mess now.
The only reason for releasing FlexConfig is that they couldnt integrate all features in the FMC UI in time. I really hope they will dump the whole CSM codebase at some point but only time will tell…
What has changed
REST API
Firepower Version 6.2.0 allows REST clients to create and configure interfaces for Firepower Threat Defense devices via the Firepower Management Center REST API. This feature enables the Firepower Management Center to interact with various Cisco products and services, as well as those from third-party vendors. Implementation of these APIs is ideal in the following scenarios:
-
large enterprises who want to control policy changes in Firepower through other Cisco systems such as Application Centric Infrastructure (ACI) or through their own proprietary orchestration solutions
-
managed security service providers who want to adopt software defined networking, application-centric infrastructure,and network function virtualization solutions
Comment
This is definitely a step in the right direction. Now we can create interface configuration using the API. If you have to create 100s of subinterfaces during a migration you will go insane. I am really looking to upcoming versions which should include CRUD operations for NAT policies and hopefully fix the ACP operations which are not working really well at the moment.
Policy Change Improvements
Deploying policy changes to a Firepower Threat Defense device can result in restarting the SNORT process and the related loss of some packets. As part of a continuing effort to address this issue, Firepower Version 6.2.0 allows you to configure actions separately for fault conditions, such as SNORT Busy/Overload or SNORT Down. This feature allows you to emphasize either continuity or security by checking a checkbox option in the Firepower Management Center.
Comment
Nice to see that users get more options to handle this issue. From my experience the snort restart is not that critical (tpc retransmissions to the rescue) but if minimal traffic loss is very critical to you, you might wanna check out the new fail-open mode.
Firepower Threat Grid API Key Integration
This feature streamlines the process of associating a Threat Grid account with your Firepower Management Center.
ISE and SGT tags without Identity
Before Firepower Version 6.2.0, you had to create a realm and identity policy to perform user control-based on ISE Security Group Tag (SGT) data, even if you did not want to configure passive authentication using ISE. In Firepower Version 6.2, you no longer need to create a realm or identity policy to perform user control-based on ISE Security Group Tag (SGT) data.
Comment
Good idea to decouple identity from SGT Tags. Not everybody wants to use ISE as identity source using pxGRID.
FTD Site-to-Site VPN Change
The site-to-site VPN with PKI support is an addition to the current capability of site-to-site VPN with pre shared keys. The Firepower Device Management (FDM) also allows you to configure site-to-site VPN with pre shared keys.
Comment
Certificate-based authentication is definitely a thing for some customers and a must have criteria for a firewall system. Nice to see that they delivered on this need.
What has been fixed?
The list of bugfixes in 6.2.0 is very long. Cisco seems to be committed to not do the same mistakes they did with 6.1.0. Back then they pushed so hard that the whole QA process seems to have failed resulting in a release with many critical bugs. To get 6.1.0 stable, 6.1.0.1 with two additional hotfix releases was needed…
I have checked all fixes and was happy to see many issues I have encountered fixed. Especially these…
CSCuy57756: In some cases, if you broke a Firepower Threat Defense high availability pair, one of the devices in the pair stayed in standalone mode and the system could not recreate the high availability pair
CSCvb19716: Resolved an issue where Firepower Management Center high availability synchronization failed if the total size of the database files and logs totaled more than 4GB.
CSCvc10655: Resolved an issue where deploying policies to a Firepower Threat Defense device failed after updating to a new version of the Firepower System.
What to expect in the near future
6.2.0.1 should be released in Q1 2017. One might think a minor release will not have any significant new features but it seems like 6.2.0.1 will finally ship AnyConnect to FTD. Coupled with some scalability improvements (I am looking at you FMC UI Performance) I look forward to 6.2.0.1 and hope AnyConnect will work stable and without limitations.